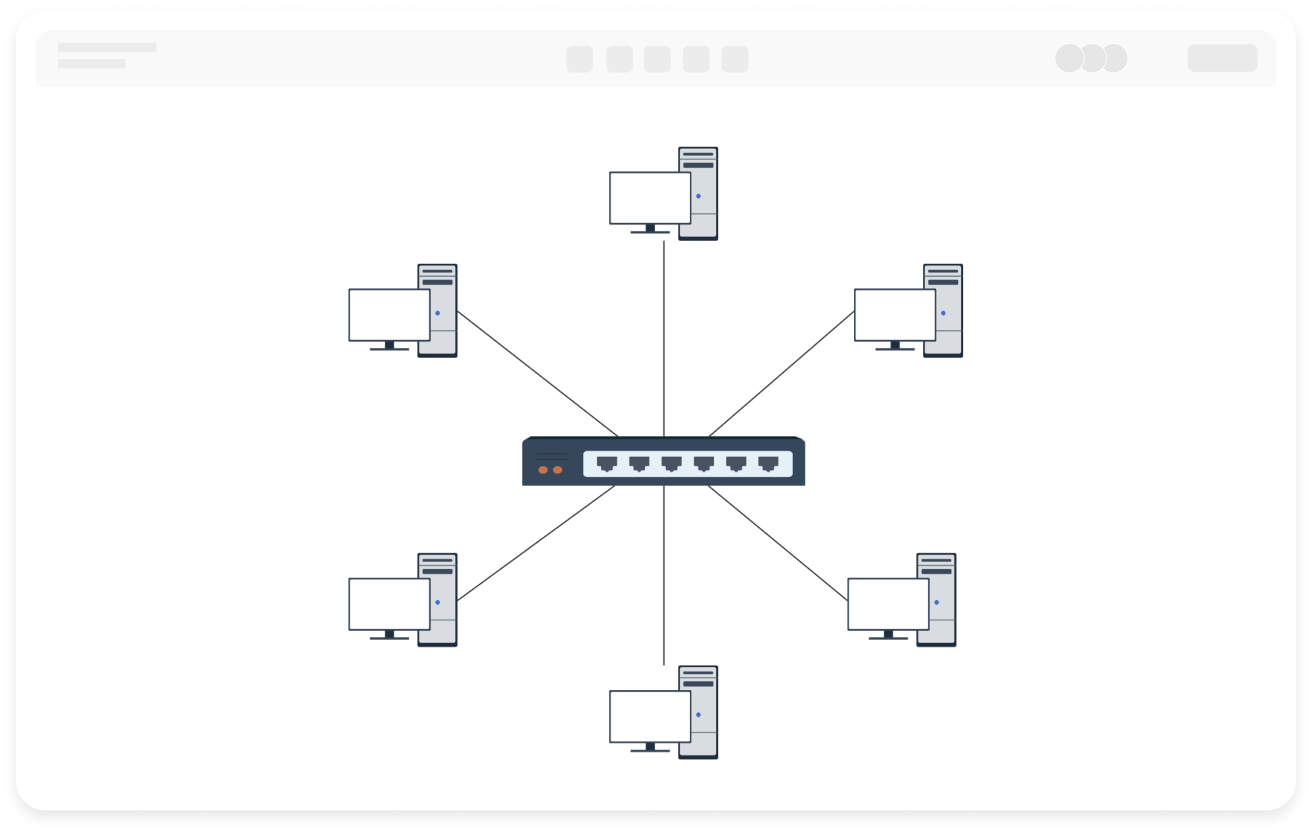
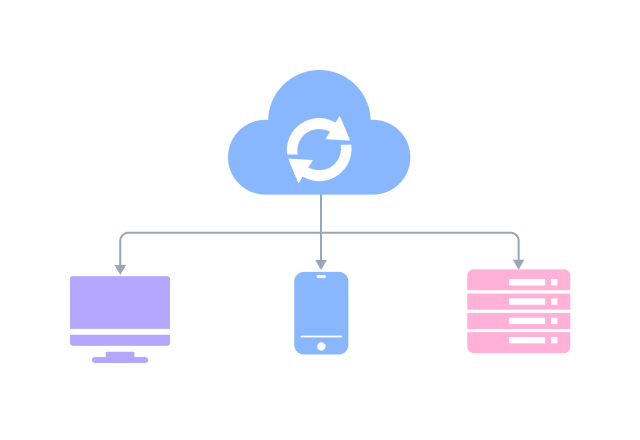
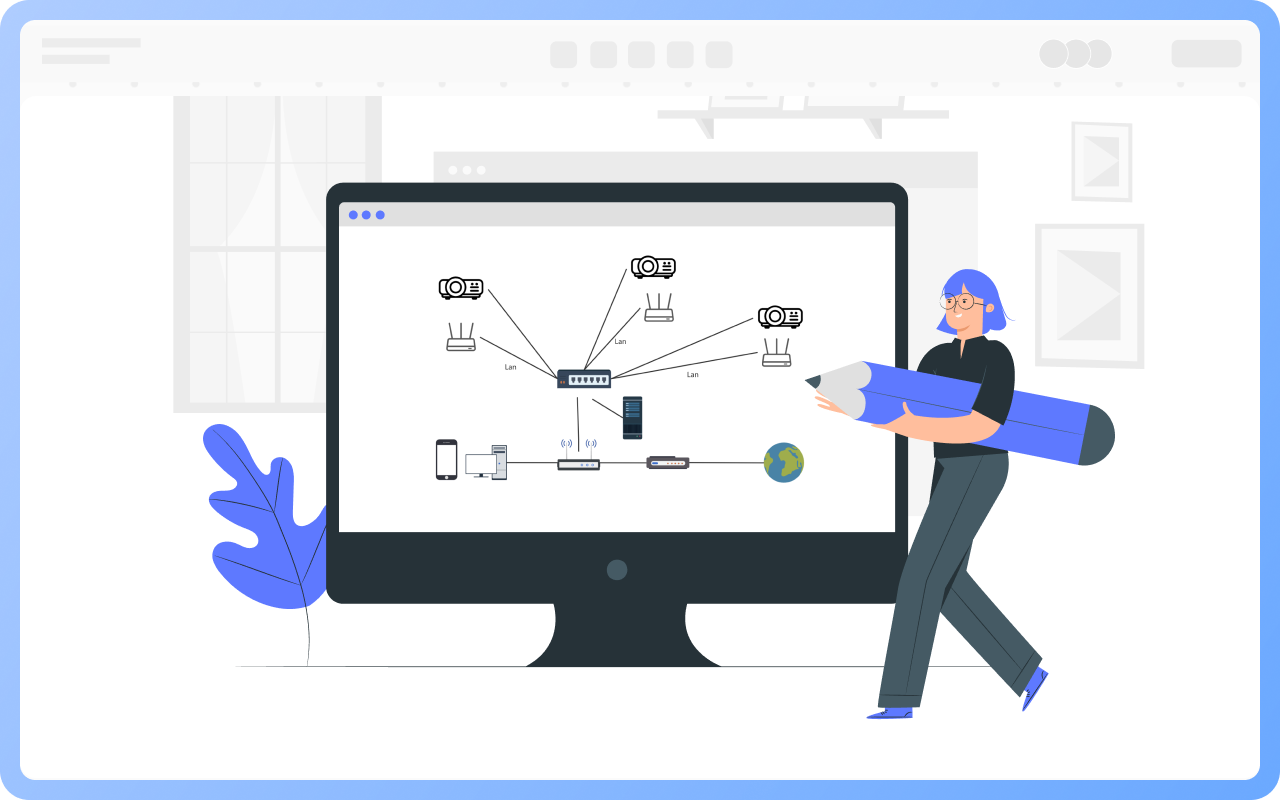
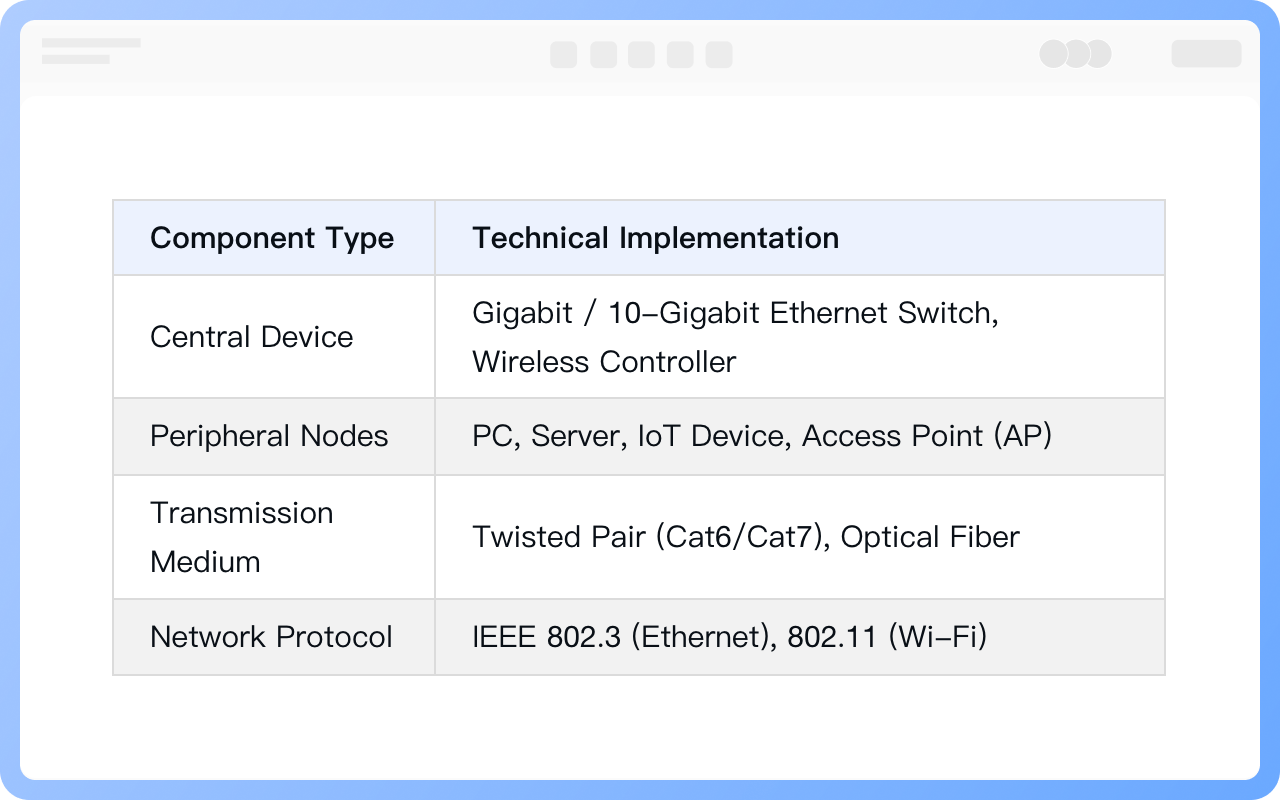
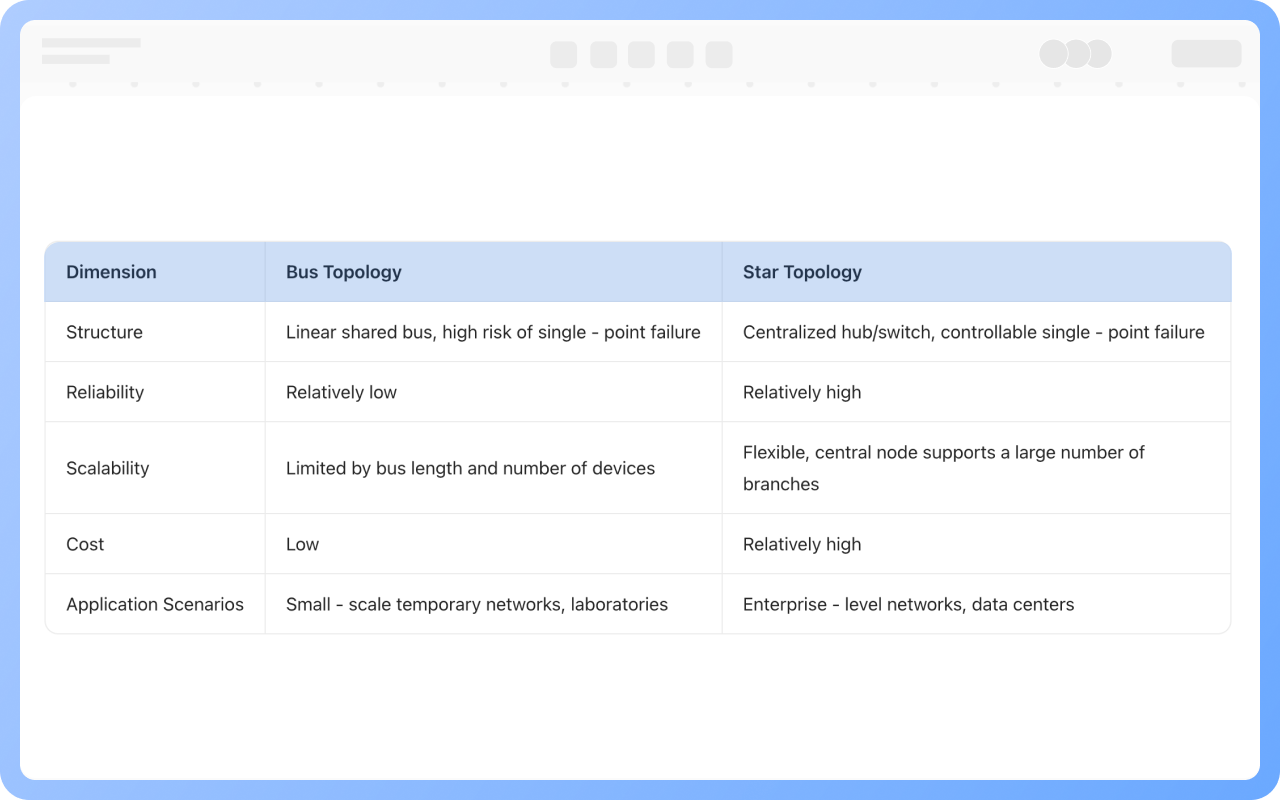
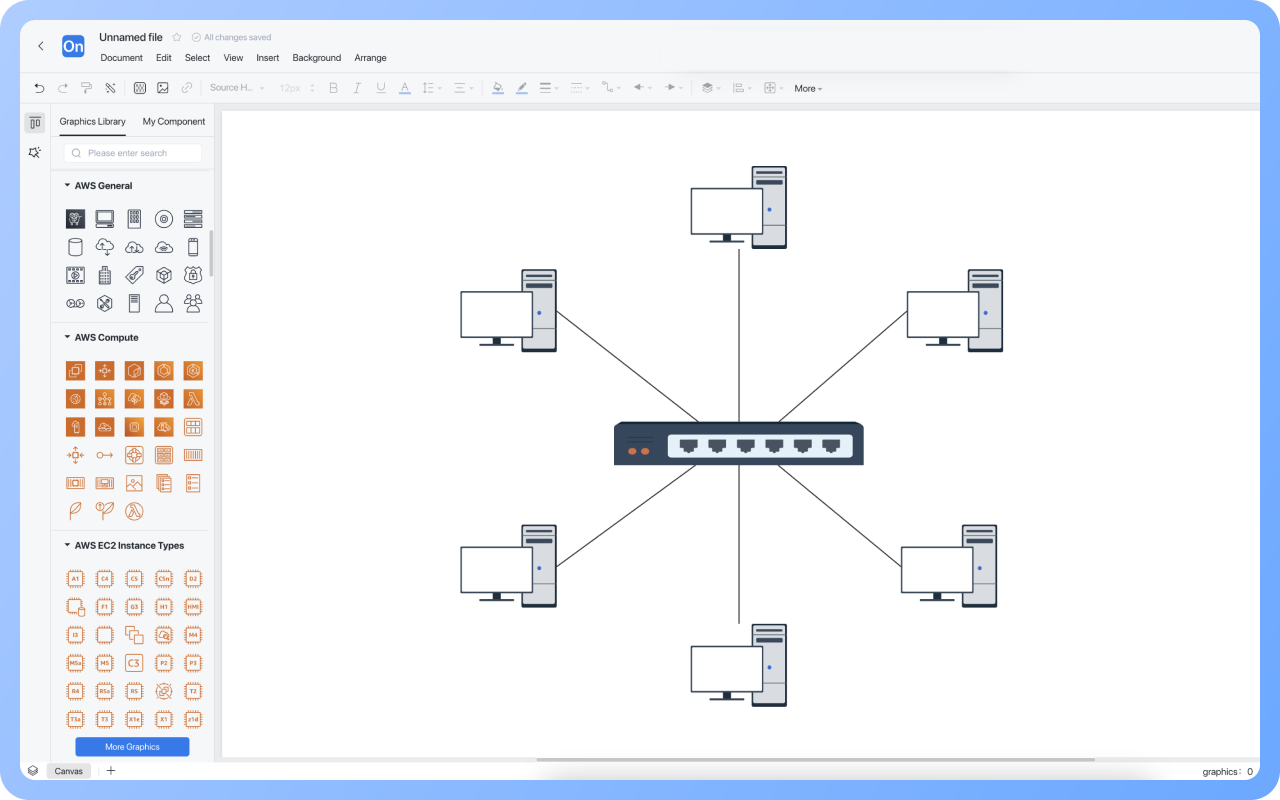
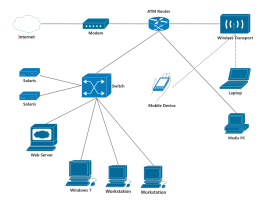
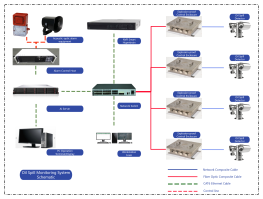
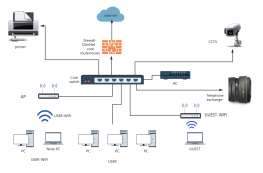
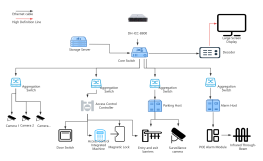
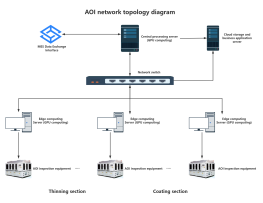
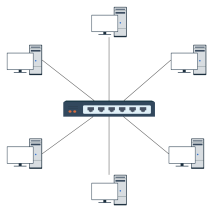
1. All data flows must pass through a central node (such as a switch or hub) to enable unified traffic monitoring, access control, and security policy deployment.
2. Failure of a single node or link will not affect the operation of other devices.
3. New nodes only need to connect to the central device, without modifying existing links.