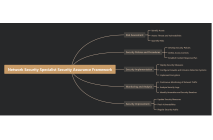
Network Security Maintenance Framework
0 Report
This Network Security Maintenance Framework mind map provides a comprehensive guide to maintaining robust network security. It emphasizes the importance of vulnerability assessment by identifying potential vulnerabilities, conducting scans and penetration tests, and prioritizing risks for remediation. The framework outlines effective patch management, including developing policies, timely application of patches, and testing for compatibility. It highlights the need for strong access control through multi-factor authentication, least privilege access, and monitoring user activity. Firewall configuration is crucial, with guidelines on maintaining rules, blocking unauthorized traffic, and monitoring logs. Intrusion detection and prevention systems are recommended to detect and block threats in real-time, with a focus on analyzing security alerts. Lastly, the framework stresses the importance of encryption and data protection, advocating for encrypting sensitive data, using secure communication protocols, and implementing data loss prevention mechanisms. Adopting these practices can significantly enhance network security and protect against potential threats.
Related Recommendations
Other works by the author
Outline/Content
See more
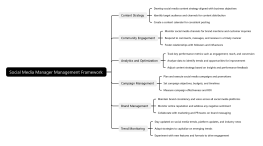
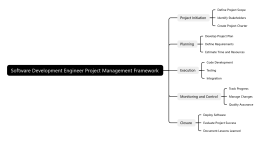
Vulnerability Assessment
Identify potential vulnerabilities in network infrastructure
Conduct vulnerability scans and penetration testing
Assess risks and prioritize vulnerabilities for remediation
Patch Management
Develop and implement patch management policies and procedures
Apply security patches and updates in a timely manner
Test patches for compatibility and effectiveness
Access Control
Implement strong authentication mechanisms (e.g., multi-factor authentication)
Enforce least privilege access controls and role-based permissions
Monitor user access and activity for unauthorized behavior
Firewall Configuration
Configure and maintain firewall rules and policies
Block unauthorized access and malicious traffic
Monitor firewall logs for security incidents and anomalies
Intrusion Detection and Prevention
Deploy intrusion detection and prevention systems (IDPS)
Detect and block intrusion attempts in real-time
Analyze and respond to security alerts and events
Encryption and Data Protection
Encrypt sensitive data in transit and at rest
Use encryption protocols such as SSL/TLS for secure communication
Implement data loss prevention (DLP) mechanisms
Collect
Collect
Collect
Collect
Collect

0 Comments
Next Page