
Five elements of information security-whole_part logic diagram
1 Report
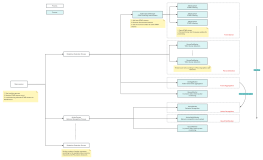
This flowchart illustrates the five essential elements of information security through a whole-part logic diagram. It highlights critical aspects such as confidentiality, ensuring that information is not exposed to unauthorized entities, and integrity, allowing only authorized personnel to modify data and detect tampering. Availability is emphasized by enabling authorized entities to access data when needed. Controllability focuses on managing the flow and behavior of information within authorized scopes, while reviewability provides the means for investigating security issues. This diagram serves as a comprehensive guide to understanding and implementing robust information security measures.
Related Recommendations
Other works by the author
Outline/Content
See more
Only authorized personnel can modify data and can identify whether the data has been tampered with
Availability
Controllability
Control the flow and behavior of information within the authorized scope
Five Elements of Information Security
Integrity
Confidentiality
Provide the basis and means for investigating the safety issues that arise
Ensure that information is not exposed to unauthorized entities or processes
Authorized entities can access data when needed
Reviewability
Collect
Collect
Collect
Collect

0 Comments
Next Page



